What Are Proxy Servers and What Are They Used For?
 |
| What Are Proxy Servers and What Are They Used For? |
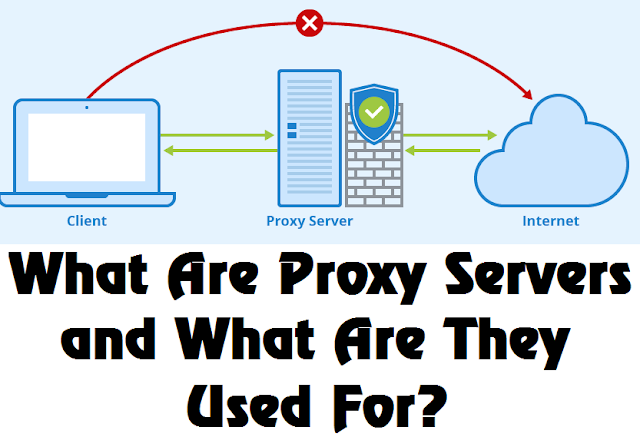
There are numerous approaches to remain mysterious on the web yet one of the most widely recognized is by utilizing what are called intermediary servers. An intermediary server is a machine that acknowledges approaching web demands and afterward advances them onto the goal; they resemble the center men of the web and keep your PC and goal web server isolated.
What this essentially implies is that when the web server gets your solicitation it looks as if it has originated from the intermediary server, hence most definitely you actually have not visited the site. There are various kinds of intermediaries however the fundamental ones are:
HTTP Proxies - These are utilized for HTTP traffic and would be significant for the above model.
Separating Proxies - These are usually found busy working and are utilized to square access to specific sites and to forestall data transfer capacity squandering; these are not utilized for security.
SOCKS Proxies - These are utilized to burrow different sorts of traffic which could incorporate emissary or ftp traffic.
Intermediaries can likewise be ordered into one of the underneath:
Mysterious - These don't recognize you to the end server and in this way keep you unknown. They can be separated into two other sub classifications - tip top and masked. A first class won't separate itself as an intermediary server to the end machine. A hidden then again will hand over enough data for the end machine to acknowledge it is an intermediary server, anyway it won't give out your IP address and along these lines your security is flawless.
As far as protection there are some different contemplations to make. Right off the bat there are a wide range of spots to obtain your intermediaries from. You can get open ones which anyone can utilize or you can utilize private ones that will cost you. Except if you are 100% certain about the source that is facilitating the intermediary you can never be too certain whether they are gathering logs and in the event that they are, well your security isn't so private all things considered!
This is the reason on the off chance that you need to have genuine feelings of serenity and appropriate security you ought to get your intermediary servers from a legitimate organization and guarantee that in their terms and conditions they express that they don't gather log records. Numerous not all that genuine organizations will gather their intermediary server from botnet invaded machines and despite the fact that this will mean you don't need to stress over any logs being gathered, it additionally implies that you are subsidizing a potential wrongdoing syndicate online that spend significant time in bringing in cash from selling contaminates machines!
Not every person needs to utilize an intermediary server to be mysterious however and you will that many individuals need to have the option to peruse locales at work that are hindered by their web channel. For this situation you would need to utilize a web intermediary. These intermediaries are fundamentally sites that permit you to peruse to different destinations, giving the site itself that has the intermediary isn't blocked you ought to have full access to any site!


Comments
Post a Comment